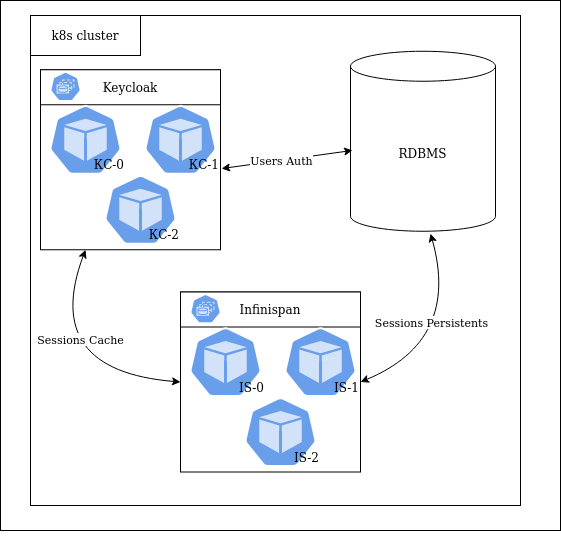
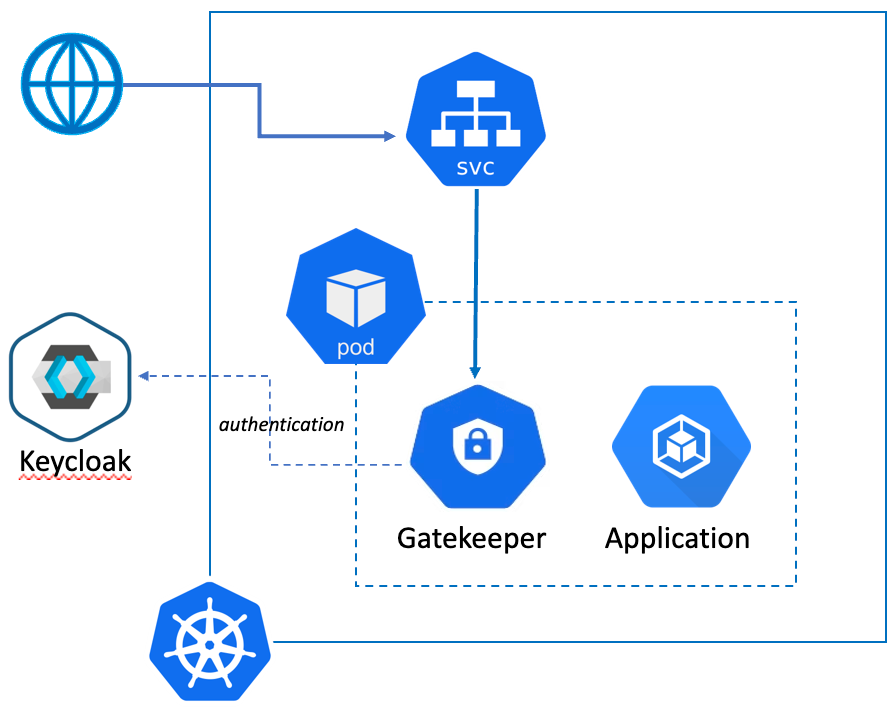
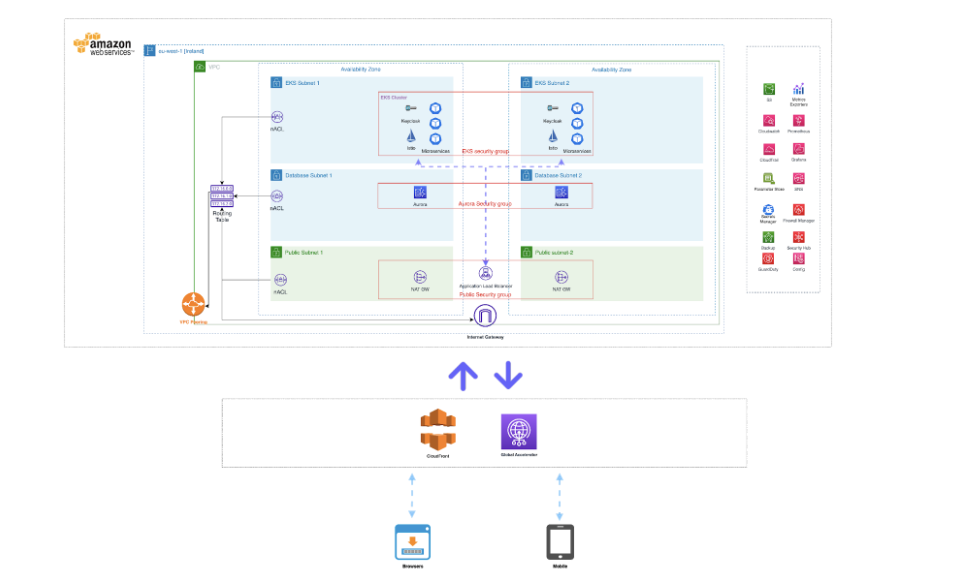
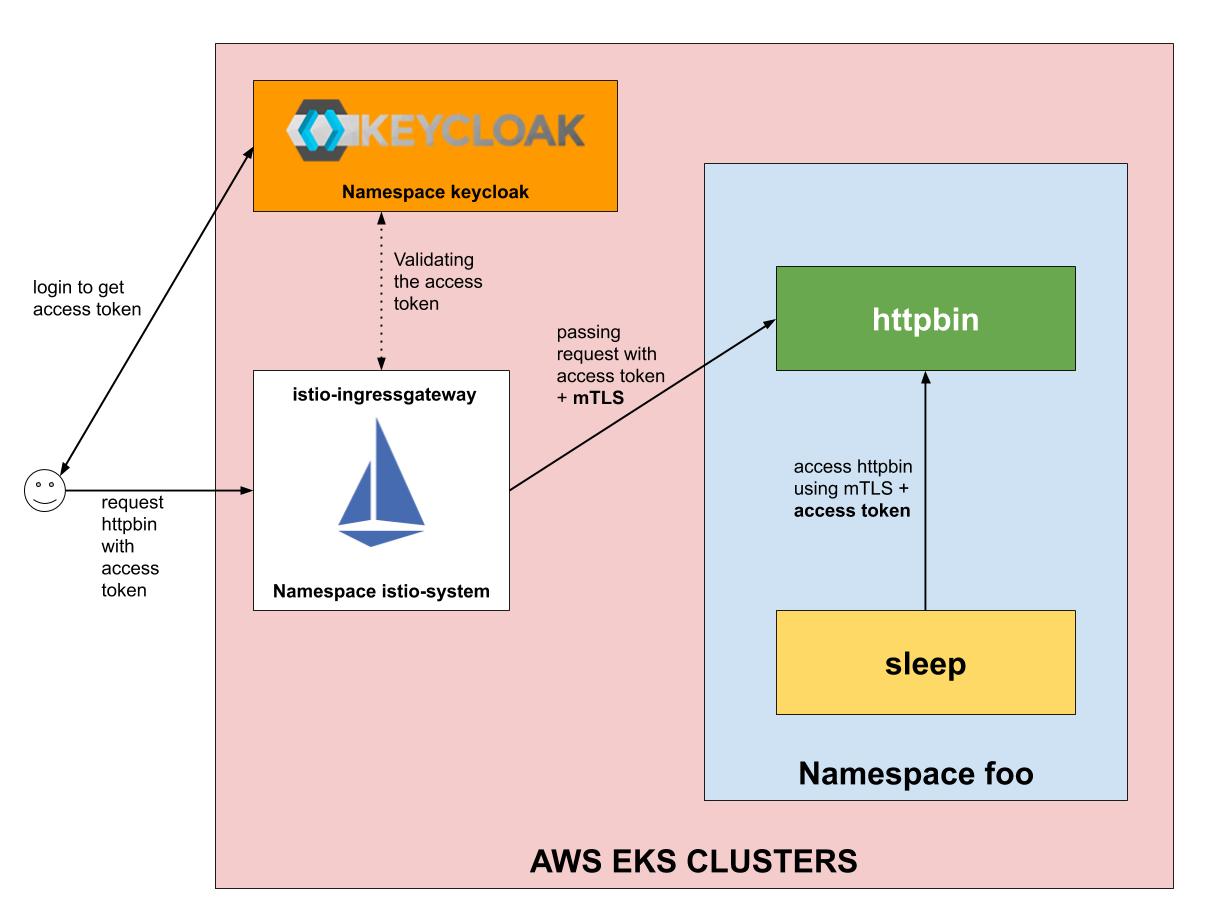
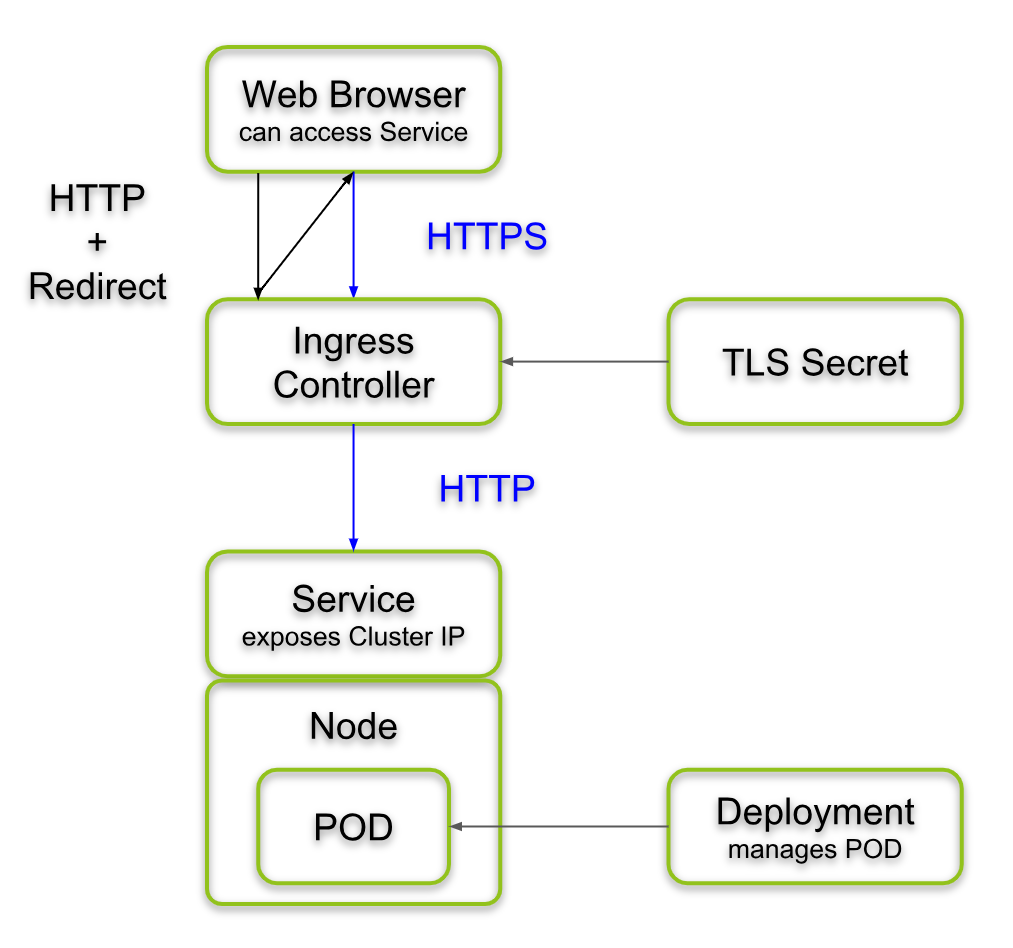
Keycloak is not accessible behind Kong Ingress Controller on Kubernetes cluster - Kong Hub - Kong Nation
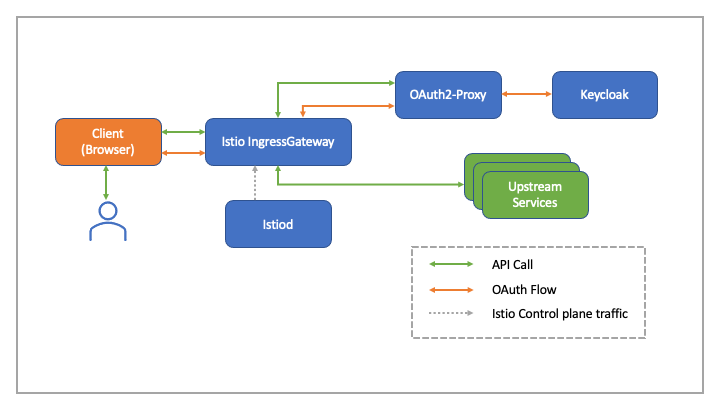
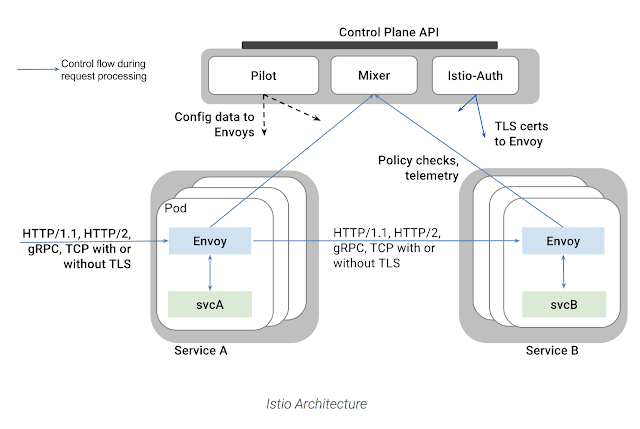
API Authentication using Istio Ingress Gateway, OAuth2-Proxy and Keycloak | by Senthil Raja Chermapandian | Medium

Authenticating with Amazon Managed Grafana Using Open Source Keycloak on Amazon EKS | AWS Open Source Blog
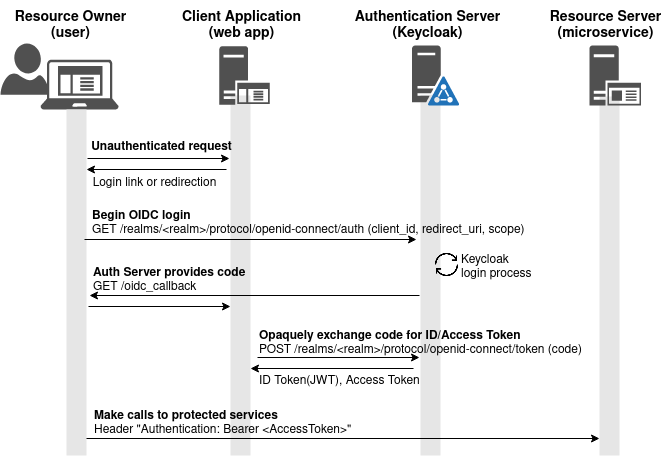
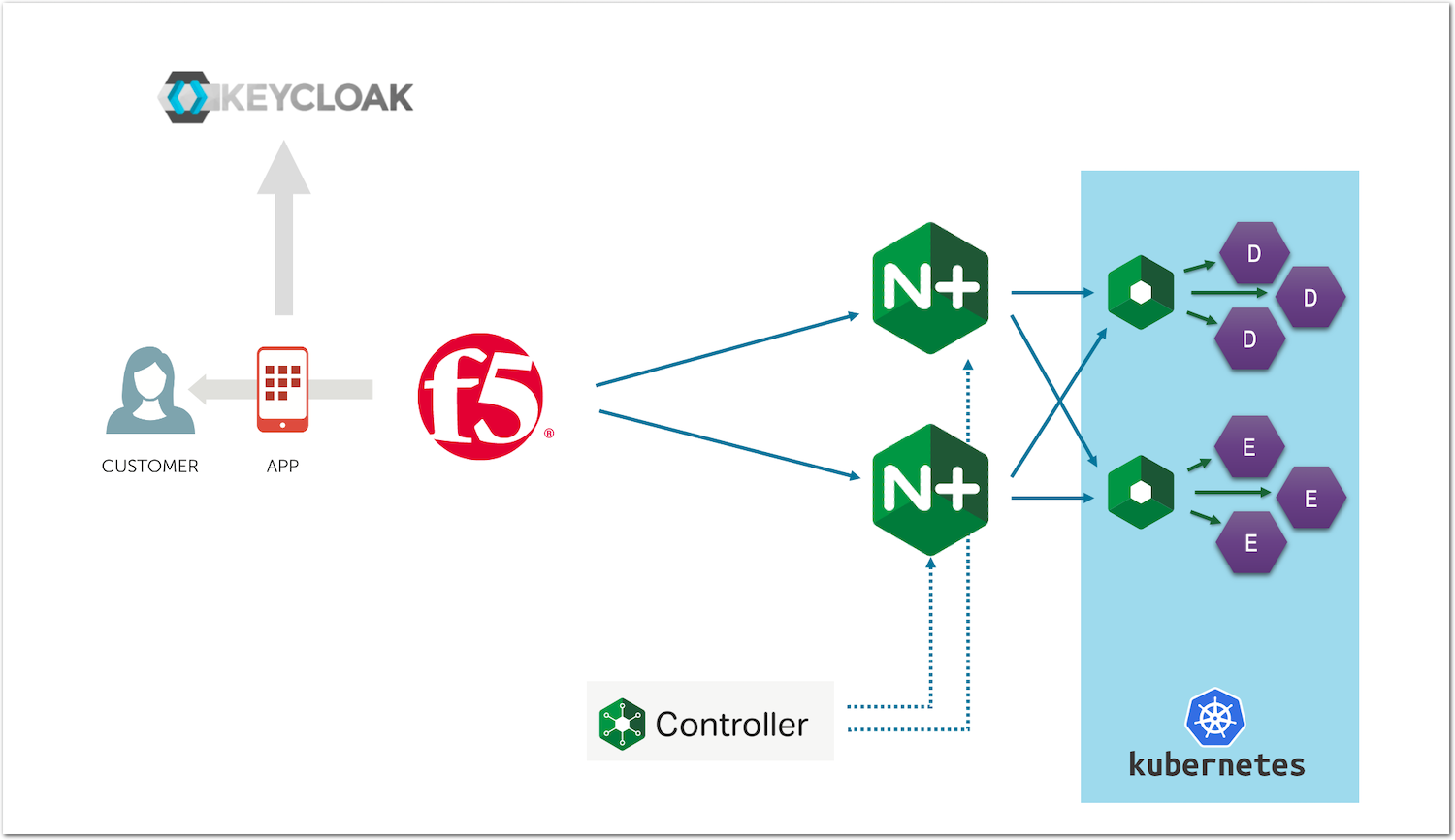
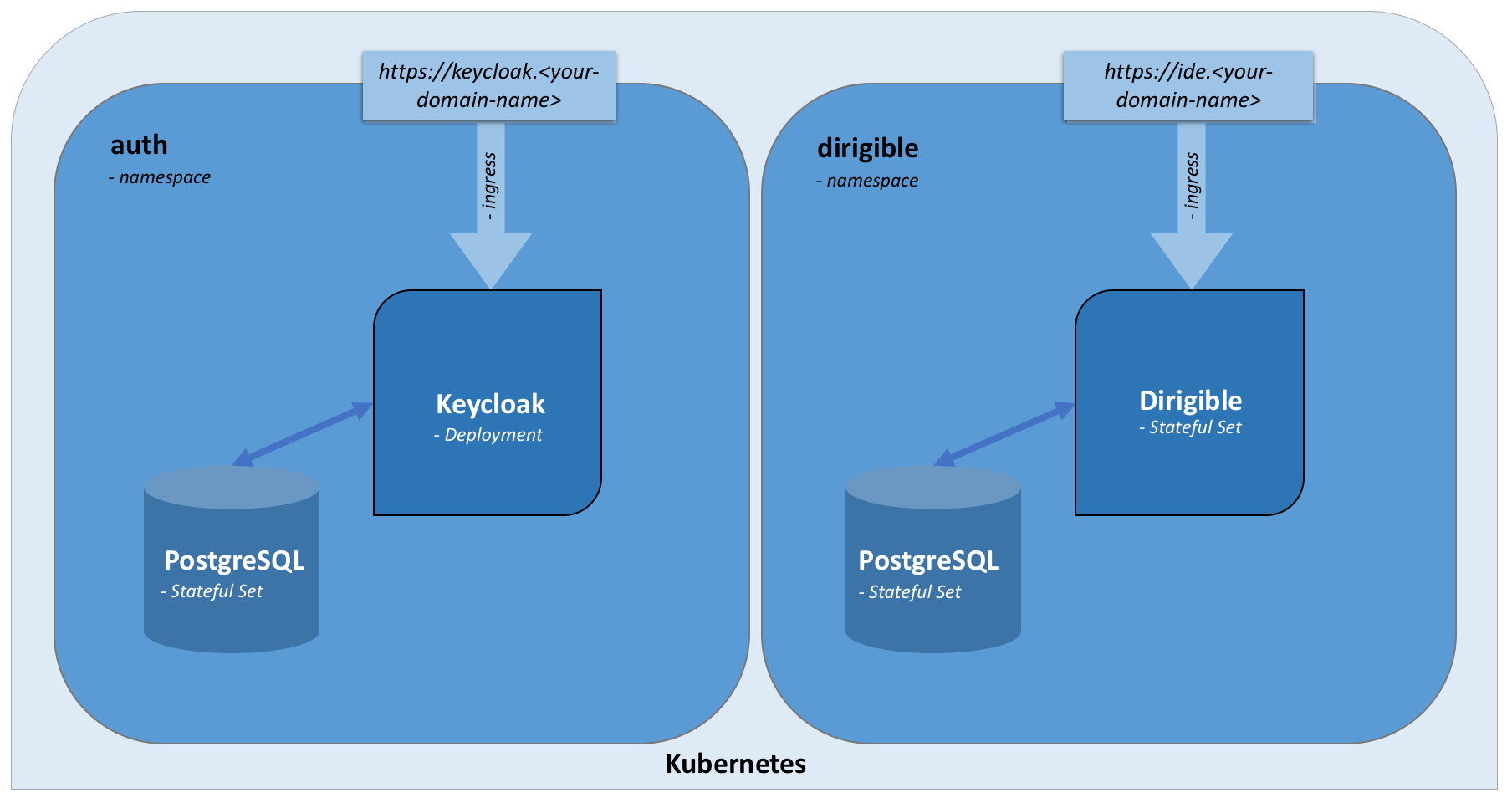
Kubernetes: Keycloak IAM deployed into Kubernetes cluster for OAuth2/OIDC | Fabian Lee : Software Engineer
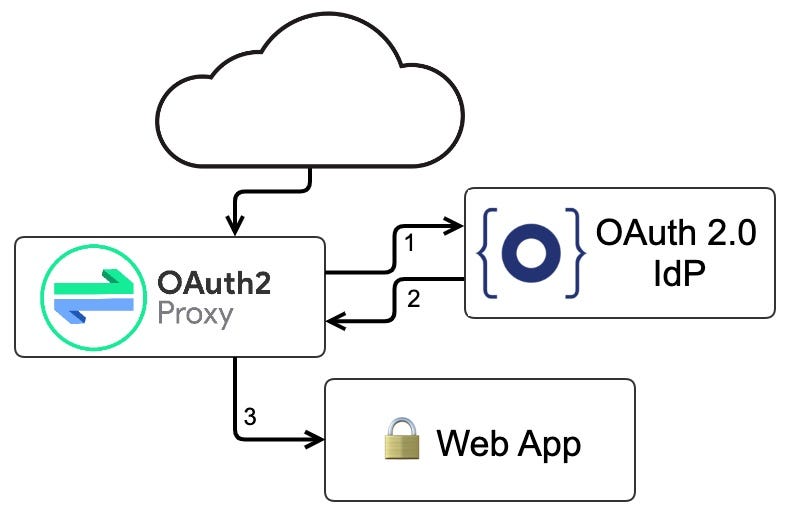
Kubernetes — Ingress External Authentication with OAuth2 Proxy and Keycloak | by Ibrahim Halil Koyuncu | Medium
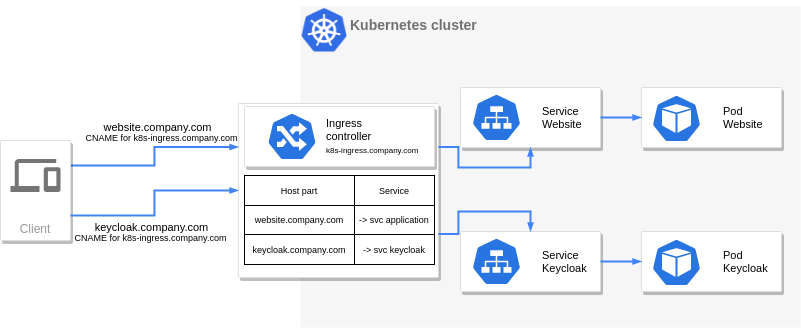
Kubernetes: SSO for web applications with Keycloak, Kerberos and Ingress Controller (and Pitfalls and Traps) | by Eric Schreiber | Medium